Recently I’ve been delving into cryptography in my free time. One of the things specifically I’ve been practicing, decoding encoded strings/scripts, ended up coming up at work. A cybersecurity researcher and teacher posted an encoded message without any context on twitter a few weeks ago that I was able to decode. The plaintext message was a url to his website with a coupon code to get one of his courses for free. I wasn’t really interested in his course I just took it as a personal challenge; I don’t even follow the guy.
So I learned a few things in the process of decoding that message. Here is the message:
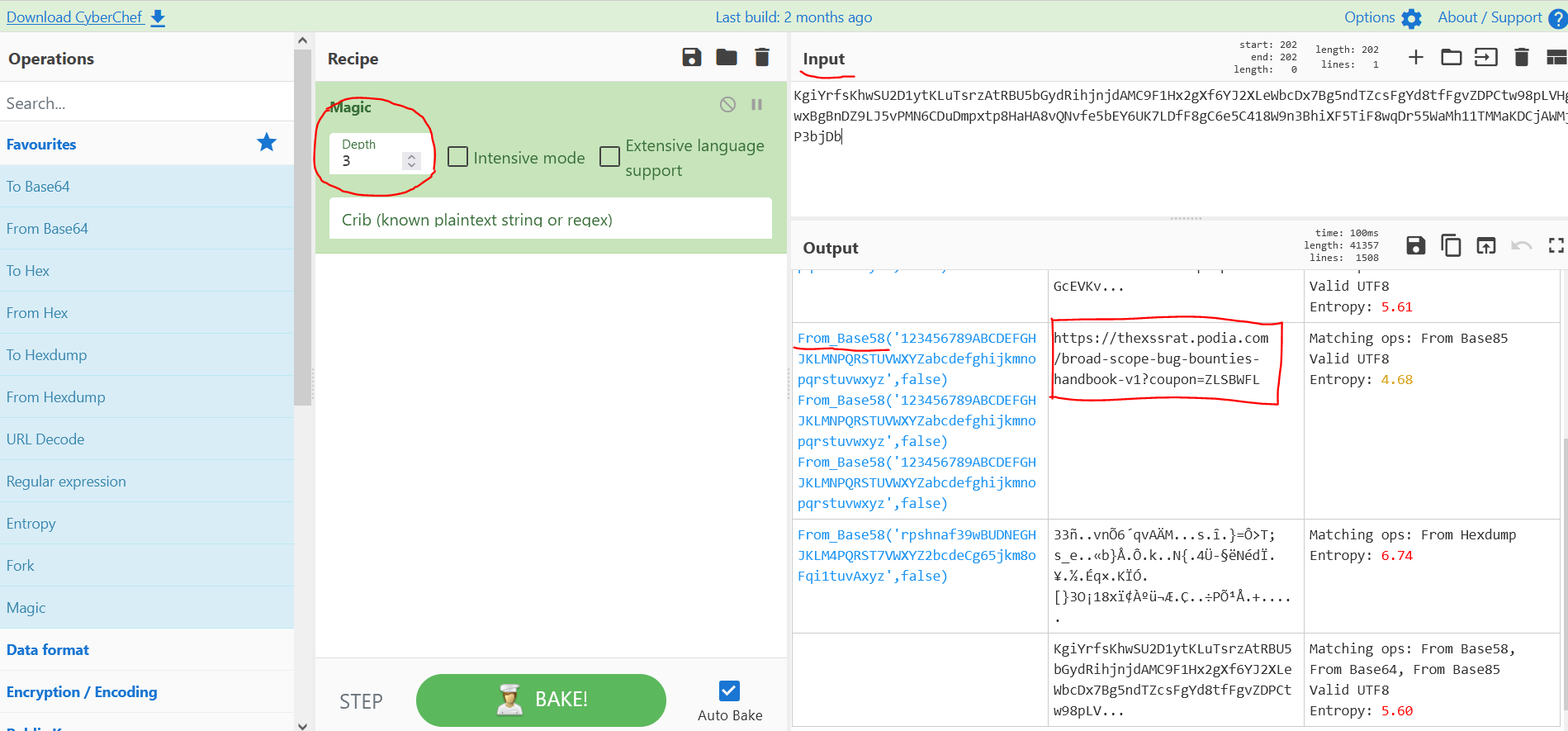
This particular string is triple encoded with base 58. There are a few tools out there you can use for situations like this but the best one I have found is Cyber Chef. Feature rich but light weight enough to run in html.
So fast forward to a week later and I run into some malware at work. A lot of what I currently do in terms of cybersecurity is review antivirus alerts, 85% of which are false positives. I won’t go into too many details but I ran across an encoded powershell script which I’m not sure I’ve seen many times before. This was at least the first time I recognized it with any degree of understanding and curiosity. For the most part it just looks like a wall of text when you see the encoded string. Later on I’ll explore what can and can’t be done with encoding in powershell but for now, here is the plaintext, decoded from base 64:
If you have the plaintext in a notepad on a Windows machine with antivirus installed it will immediately detect it as a threat and try to quarantine it, just the text of the command! The plaintext script itself is pretty advanced and it’s full purpose isn’t immediately clear. As best I can tell it's fetching a powershell payload on internet, decrypting it $R $IV $K and executing it | IEX Pretty interesting stuff.